Intro
This blog site becomes part of our Admin Basics series, where we’ll concentrate on subjects essential to those handling and keeping Databricks environments. See our previous blog sites on Office Company, Office Administration, UC Onboarding, and Cost-Management finest practices!
Information ends up being helpful just when it is transformed to insights. Information democratization is the self-serve procedure of getting information into the hands of individuals that can include worth to it without excessive procedure traffic jams and without pricey and awkward synthetic pas minutes. There are countless circumstances of unintentional errors such as a malfunctioning inquiry released by a junior information expert as a “SELECT * from << huge table here>>” or perhaps an information enrichment procedure that does not have suitable sign up with filters and secrets. Governance is required to prevent anarchy for users, guaranteeing right gain access to advantages not just to the information however likewise to the underlying calculate required to crunch the information. Governance of an information platform can be burglarized 3 primary locations – Governance of Users, Data & & Compute.
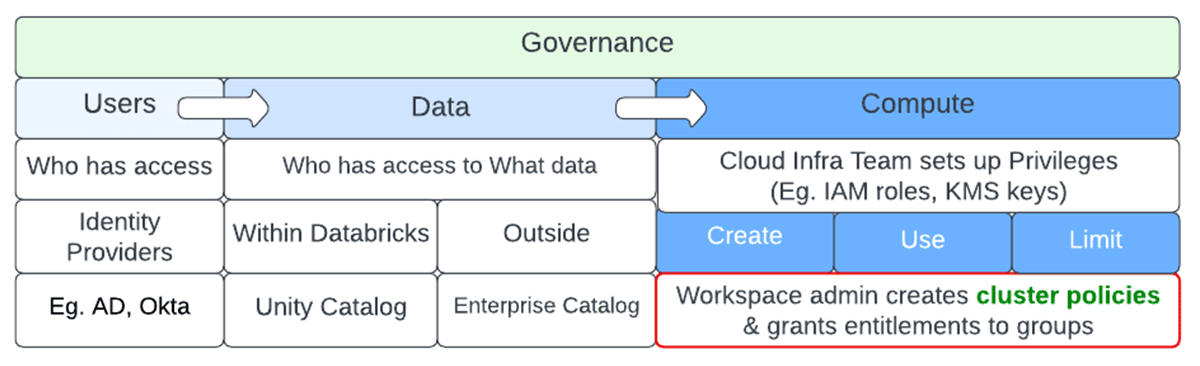
Governance of users makes sure the best entities and groups have access to information and calculate. Enterprise-level identity companies generally impose this and this information is synced to Databricks. Governance of information identifies who has access to what datasets at the row and column level. Business brochures and Unity Brochure assistance impose that. The most pricey part of an information pipeline is the underlying calculate It generally needs the cloud infra group to establish advantages to help with gain access to, after which Databricks admins can establish cluster policies to guarantee the best principals have access to the required calculate controls. Please describe the repo to follow along.
Advantages of Cluster Policies
Cluster Policies act as a bridge in between users and the cluster usage-related advantages that they have access to. Simplification of platform use and efficient expense control are the 2 primary advantages of cluster policies. Users have less knobs to attempt causing less unintentional errors, particularly around cluster sizing. This results in much better user experience, enhanced efficiency, security, and administration lined up to business governance. Setting limitations on max use per user, per work, per hour use, and restricting access to resource types whose worths add to cost assists to have foreseeable use costs. Eg. limited node type, DBR variation with tagging and autoscaling. ( AWS, Azure, GCP)
Cluster Policy Meaning
On Databricks, there are a number of methods to raise calculate resources – from the Clusters UI, Jobs releasing the defined calculate resources, and by means of REST APIs, BI tools (e.g. PowerBI will self-start the cluster), Databricks SQL Dashboards, ad-hoc inquiries, and Serverless inquiries.
A Databricks admin is entrusted with developing, releasing, and handling cluster policies to specify guidelines that determine conditions to develop, utilize, and limitation calculate resources at the business level. Generally, this is adjusted and fine-tuned by the numerous Line of work (LOBs) to satisfy their requirements and line up with enterprise-wide standards. There is a great deal of versatility in specifying the policies as each control aspect provides a number of methods for setting bounds. The numerous characteristics are noted here
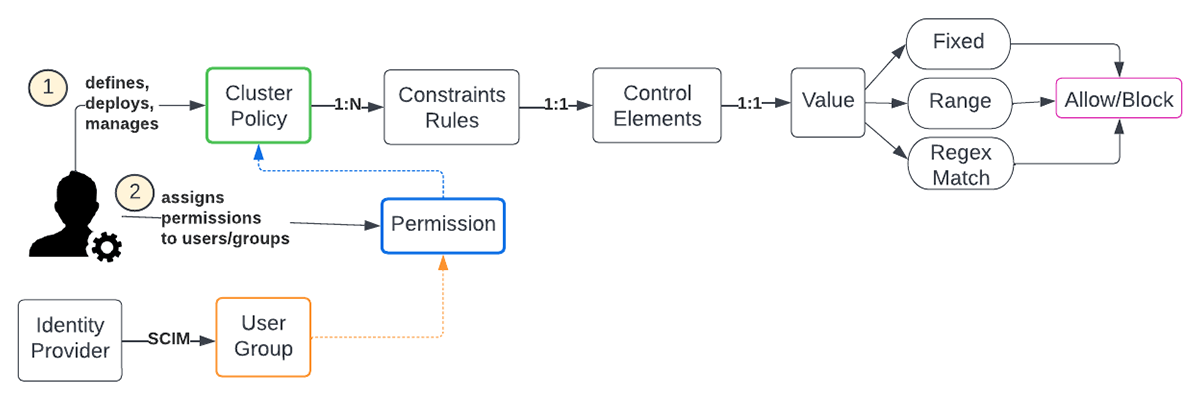
Workspace admins have consent to all policies. When developing a cluster, non-admins can just choose policies for which they have actually been approved consent. If a user has cluster develop consent, then they can likewise choose the Unlimited policy, enabling them to develop fully-configurable clusters. The next concern is the number of cluster policies are thought about enough and what is a great set, to start with.
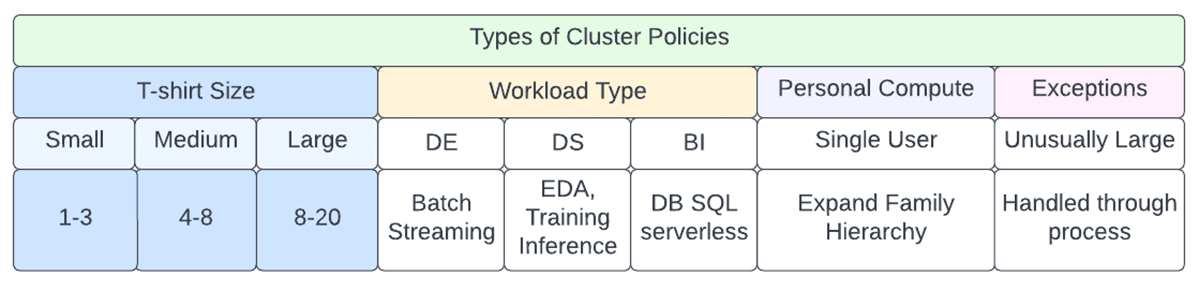
There are basic cluster policy households that are offered out of package at the time of work space implementation (These will become relocated to the account level) and it is highly suggested to utilize them as a base design template. When utilizing a policy household, policy guidelines are acquired from the policy household. A policy might include extra guidelines or bypass acquired guidelines.
The ones that are presently provided consist of
- Individual Compute & & Power User Compute (single user utilizing versatile cluster)
- Shared Compute (multi-user, versatile cluster)
- Task Compute (task Compute)
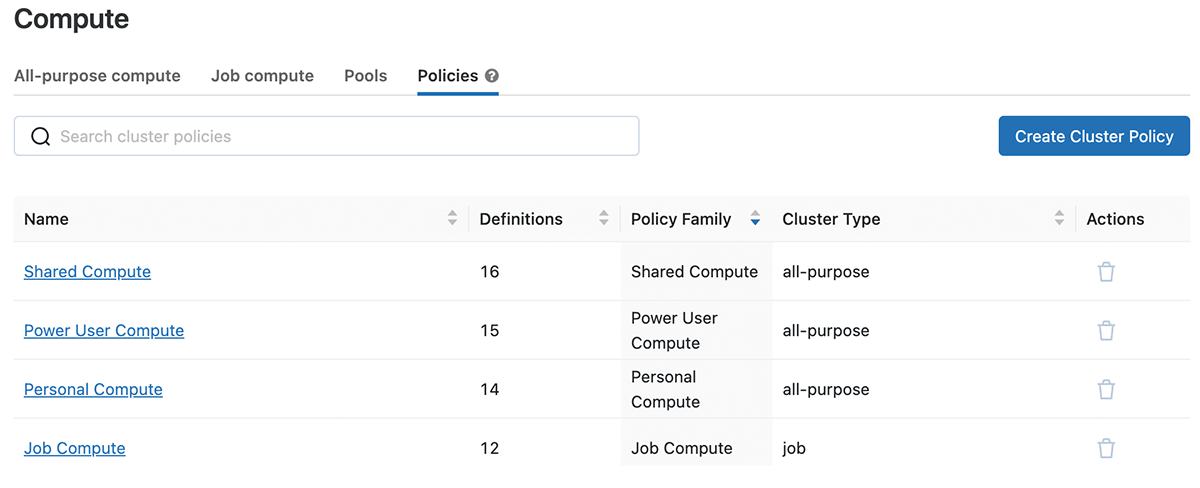
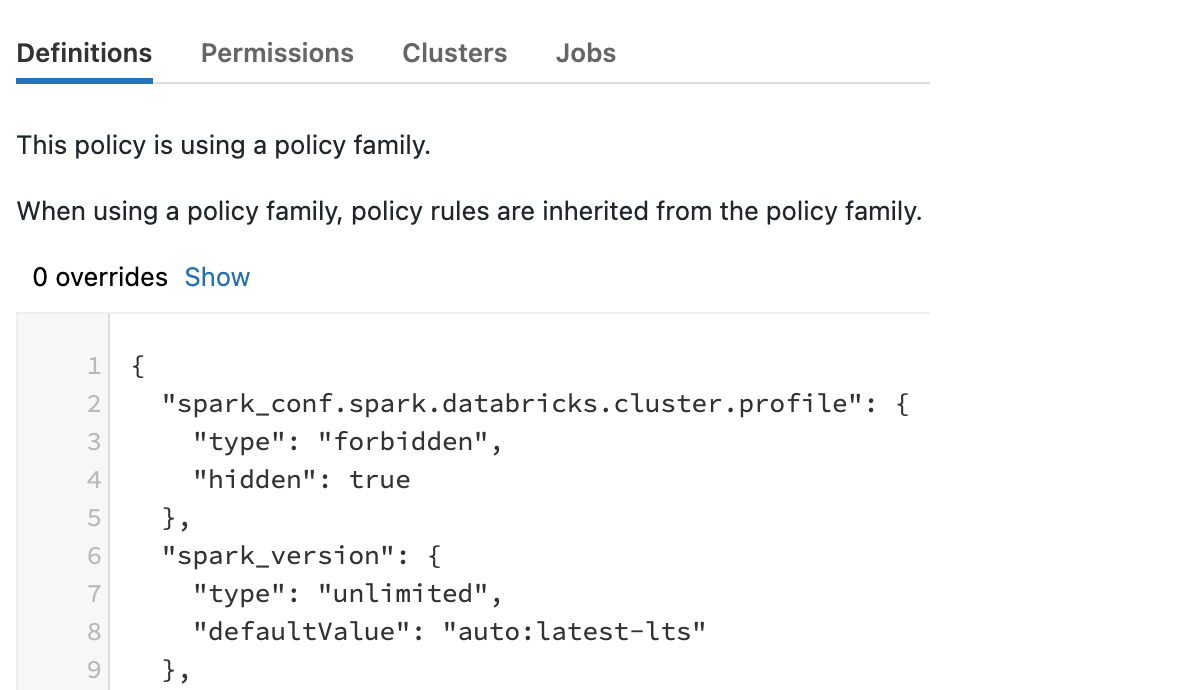
Clicking into among the policy households, you can see the JSON meaning and any overrides to the base, authorizations, clusters & & tasks with which it is associated.
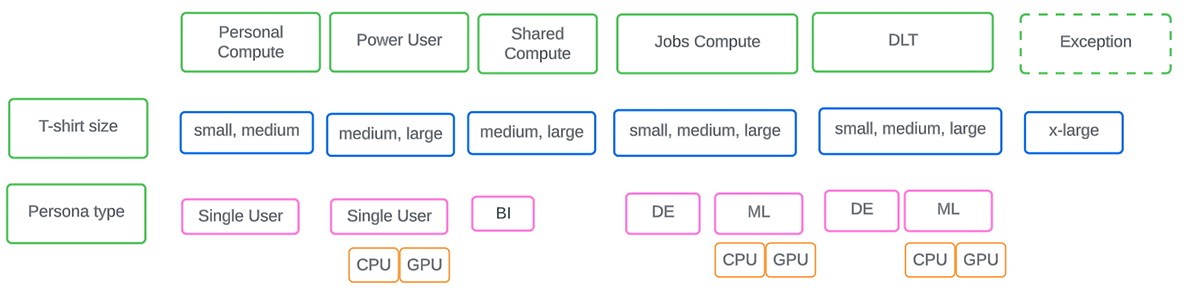
There are 4 cluster households that come predefined that you can utilize as-is and supplement with others to match the diverse requirements of your company. Describe the diagram listed below to prepare the preliminary set of policies that require to be in location at a business level thinking about work type, size, and personality included.
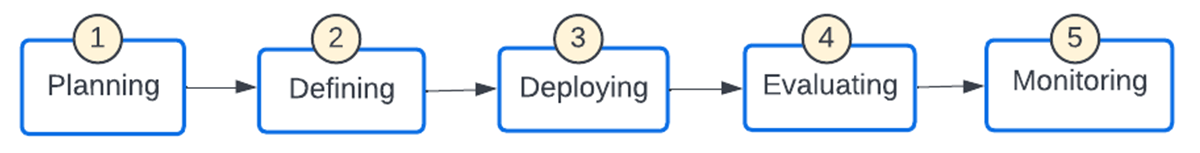
Rolling out Cluster Policies in a business
- Preparation: Articulate business governance objectives around managing the spending plan, and use attribution by means of tags so that expense centers get precise chargebacks, runtime variations for compatibility and assistance requirements, and regulative audit requirements.
- The ‘ unlimited’ cluster policy privilege offers a backdoor path for bypassing the cluster policies and need to be reduced for non-admin users. This setting is offered in the work space settings for users. In addition, think about offering just ‘ Can Reboot‘ for interactive clusters for the majority of users.
- The procedure need to manage exception circumstances eg. ask for an uncommonly big cluster utilizing an official approval procedure. Secret success metrics need to be specified so that the efficiency of the cluster policies can be measured.
- A great identifying convention assists with self-describing and management requires so that a user naturally understands which one to utilize and an admin acknowledges which LOB it comes from. For eg. mkt_prod_analyst_med represents the LOB, environment, personality, and tee shirt size.
- Budget Plan Tracking API (Personal Sneak peek) function enables account administrators to set up regular or one-off budget plans for Databricks use and get e-mail notices when limits are gone beyond.
- Specifying: The initial step is for a Databricks admin to make it possible for Cluster Gain Access To Control for a premium or greater work space. Admins need to develop a set of base cluster policies that are acquired by the LOBs and adjusted.
- Releasing: Cluster Policies need to be thoroughly thought about prior to rollout. Regular modifications are not perfect as it puzzles completion users and does not serve the desired function. There will be events to present a brand-new policy or modify an existing one and such modifications are best done utilizing automation. As soon as a cluster policy has actually been altered, it impacts consequently developed calculate. The “Clusters” and “Jobs” tabs note all clusters and tasks utilizing a policy and can be utilized to determine clusters that might be out-of-sync.
- Examining: The success metrics specified in the preparation stage need to be assessed on a continuous basis to see if some tweaks are required both at the policy and procedure levels.
- Tracking: Regular scans of clusters need to be done to guarantee that no cluster is being spun up without an associated cluster policy.
Cluster Policy Management & & Automation
Cluster policies are specified in JSON utilizing the Cluster Policies API 2.0 and Permissions API 2.0 ( Cluster policy authorizations) that handle which users can utilize which cluster policies. It supports all cluster characteristics managed with the Clusters API 2.0, extra artificial characteristics such as max DBU-hour, and a limitation on the source that produces a cluster.
The rollout of cluster policies need to be correctly checked in lower environments prior to rolling to prod and interacted to the groups ahead of time to prevent unintentional task failures on account of insufficient cluster-create advantages. Older clusters keeping up previous variations require a cluster edit and reboot to embrace the more recent policies either through the UI or REST APIs. A soft rollout is suggested for production, in which in the very first stage just the tagging part is implemented, when all groups offer the green signal, relocate to the next phase. Ultimately, get rid of access to unlimited policies for limited users to guarantee there is no backdoor to bypass cluster policy governance. The following diagram reveals a phased rollout procedure:
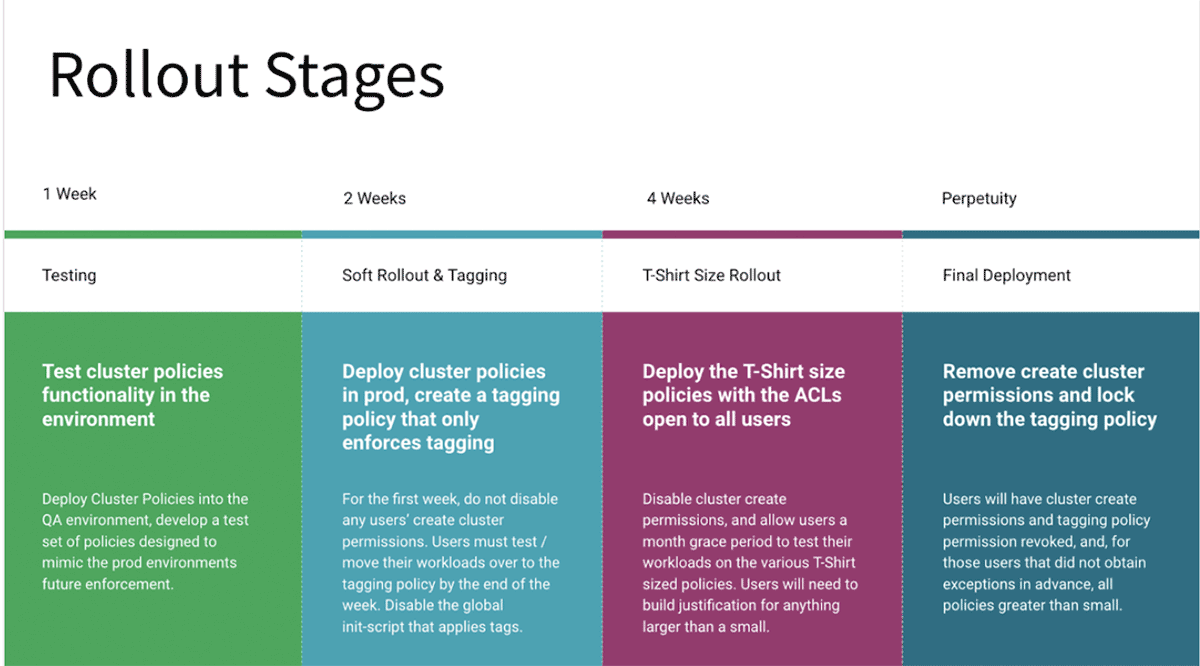
Automation of cluster policy rollout makes sure there are less human mistakes and the figure listed below is a suggested circulation utilizing Terraform and Github
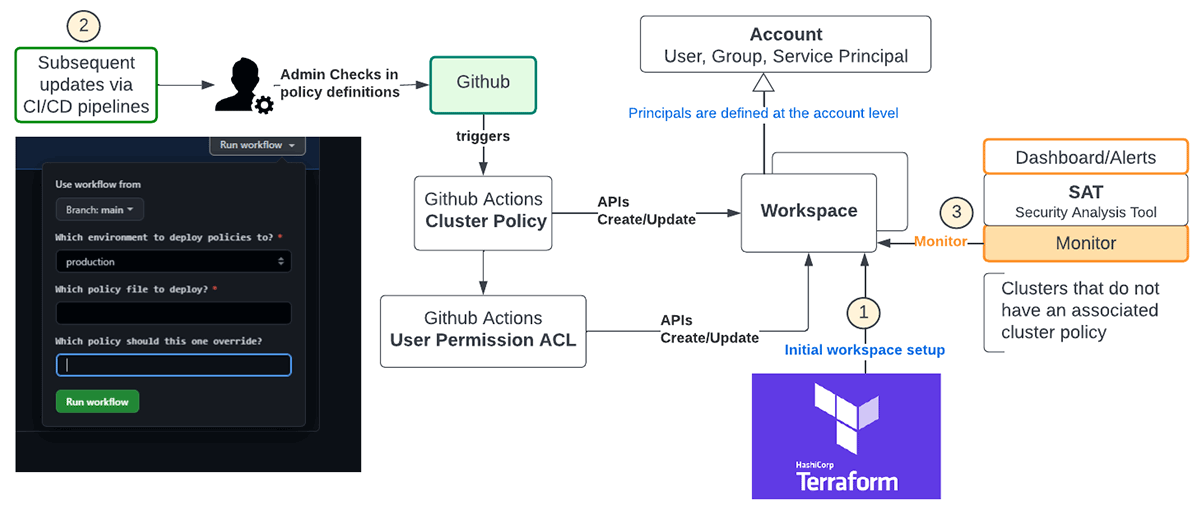
- Terraform is a multi-cloud requirement and needs to be utilized for releasing brand-new work areas and their associated setups. For instance, this is the design template for instantiating these policies with Terraform, which has actually the included advantage of keeping state for cluster policies.
- Subsequent updates to policy meanings throughout work areas need to be handled by admin personalities utilizing CI/CD pipelines. The diagram above programs Github workflows handled by means of Github actions to release policy meanings and the associated user authorizations into the picked work areas.
- REST APIs can be leveraged to keep an eye on clusters in the work space either clearly or implicitly utilizing the SAT tool to guarantee enterprise-wide compliance.
Delta Live Tables (DLT)
DLT streamlines the ETL procedures on Databricks. It is suggested to use a single policy to both the default and upkeep DLT clusters. To set up a cluster policy for a pipeline, develop a policy with the cluster_type field set to dlt as revealed here
External Metastore
If there is a requirement to connect to an admin-defined external metastore, the following design template can be utilized.
Serverless
In the lack of a serverless architecture, cluster policies are handled by admins to expose control knobs to develop, handle and restrict calculate resources. Serverless will likely ease this duty off the admins to a specific level. Regardless, these knobs are needed to supply versatility in the development of calculate to match the particular requirements and profile of the work.
Summary
To sum up, Cluster Policies have enterprise-wide exposure and make it possible for administrators to:
- Limitation expenses by managing the setup of clusters for end users
- Simplify cluster development for end users
- Implement tagging throughout their work space for expense management
CoE/Platform groups need to prepare to roll these out as they have the capacity of generating much-needed governance, and yet if not done correctly, they can be entirely inadequate. This isn’t practically expense savings however about guardrails that are necessary for any information platform.
Here are our suggestions to guarantee efficient application:
- Begin with the preconfigured cluster policies for 3 popular usage cases: individual usage, shared usage, and tasks, and extend those by tee shirt size and personality type to deal with work requirements.
- Plainly specify the identifying and tagging conventions so that LOB groups can acquire and customize the base policies to match their circumstances.
- Develop the modification management procedure to enable brand-new ones to be included or older ones to be fine-tuned.
Please describe the repo for instances to begin and release Cluster Policies