In my preceding post, I assured to offer more examples highlighting the significance of software application sustainment in the U.S. Department of Defense (DoD). My focus is on sustaining tradition weapons systems that are no longer in production, however are anticipated to stay a crucial element of our defense ability for years to come. Regardless of the truth that these tradition systems are no longer in the acquisition stage, software application upgrade cycles are required to revitalize their abilities every 18 to 24 months. In addition, substantial modernization can frequently be made by more comprehensive, focused software application upgrades with reasonably modest hardware modifications. This 3rd post explains efficient sustainment engineering efforts in the Army, utilizing examples from throughout its software application engineering centers These examples are connected to SEI research study on ability maturity designs, dexterity, and the Architecture Analysis and Style Language (AADL) modeling notation.
A Short History of Software Application Sustainment in the Army
From its earliest days, the armed force has actually supplied centers to keep the performance of its numerous weapon systems. The detailed terms for these systems have actually consisted of “toolboxes,” “depots,” and “engineering centers,” among others. In the Army, duty remains in software application centers within the Research Study, Advancement, and Engineering Command (RDECOM) Websites are spread out throughout the nation, from New Jersey ( Picatinny Toolbox) and Maryland ( Aberdeen Proving Ground) to Arizona ( Fort Huachuca).
Within this geographical structure of toolboxes and depots throughout the nation, we can overlay the increased significance of software application in our weapon systems. The Abrams Main Fight Tank offers an exceptional example. Style started in 1972, with production in 1980. Existing forecasts are that the most recent variation (M1A2) will stay in usage another thirty years, stressing the requirement for software application updates to tradition weapon systems. Likewise, the Army’s Apache helicopter has actually experienced exceptional, software-intense upgrades over its life given that its preliminary style in the 1970s. The preliminary variation, the AH-64A, had about 300,000 source lines of code (KSLOC) aboard. The AH-64D, produced more just recently, has more than 1.4 million source lines of code (MSLOC), greatly broadening the abilities of the system. The just recently launched AH-64E continues the development of software application significance in this pillar of Army air travel (more about this weapon system later on in this publishing).
Offered the growing significance of software application for Army systems, this post highlights some current examples of efficient sustainment of software-reliant systems throughout RDECOM. I concentrate on the outcomes of enhancement efforts throughout the domain. The labor force in the software application centers has actually grown in its technical skills, and a modern-day systems engineering environment has actually been established. With that historic point of view, we can check out a few of the examples obvious today.
Constant Enhancement
The Weaponry Software Application Engineering Center (Weaponry SEC) at Picatinny Toolbox has actually long been included with SEI innovations. In keeping with the principle that reaching maturity levels utilizing designs like CMMI just sets the phase for higher enhancements, the Weaponry SEC group at the toolbox has actually shared its method to flaw containment with their REDCOM peers. The chart listed below programs the group’s Problem Containment Matrix (DCM), which offers a method of aesthetically showing info about the problems and issue reports related to a system.
Problem Containment Matrix Example
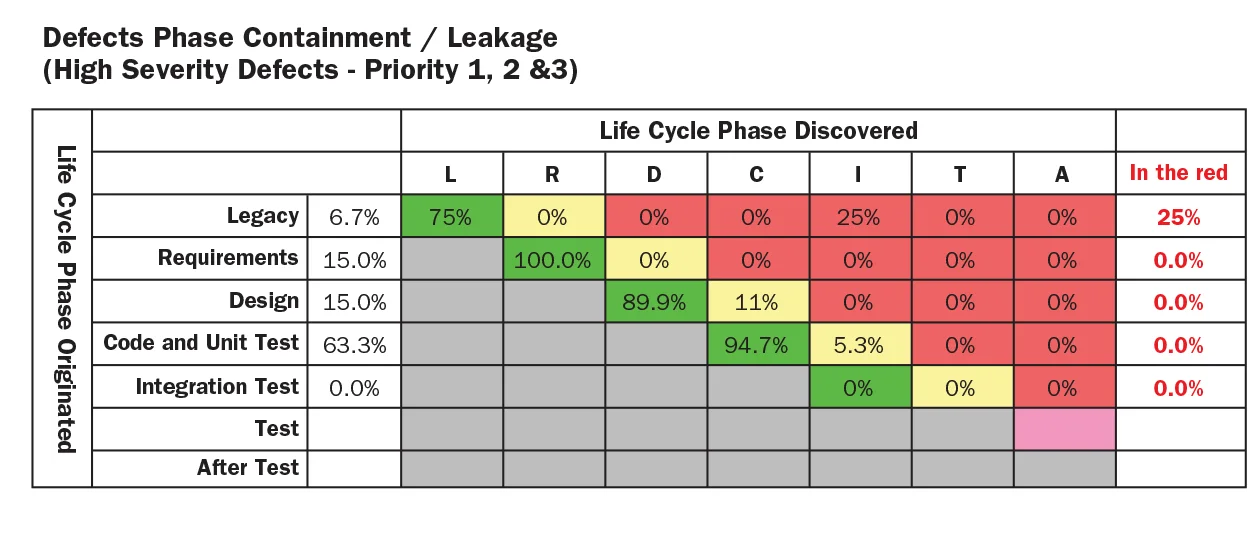
Source: ARDEC Weaponry Software Application Engineering Center (Picatinny Toolbox)
By utilizing a DCM technique, the Weaponry SEC group can focus its enhancement efforts on the locations that the majority of require it. This matrix allows advancement groups to enhance their concentrate on getting rid of problems so they do not leakage into the next stage of the lifecycle. This procedure permits earlier corrections and conserves rework expenses.
The Problem Leak Enhancement chart listed below programs the advantage to the Weaponry SEC flaw elimination procedure from various procedure enhancements, such as boosted software application peer evaluations Metrics recorded throughout the enhancement cycle, from when the center had actually been carrying out at maturity level 3 to its present status at maturity level 5, inform the story.
Problem Leak Enhancement
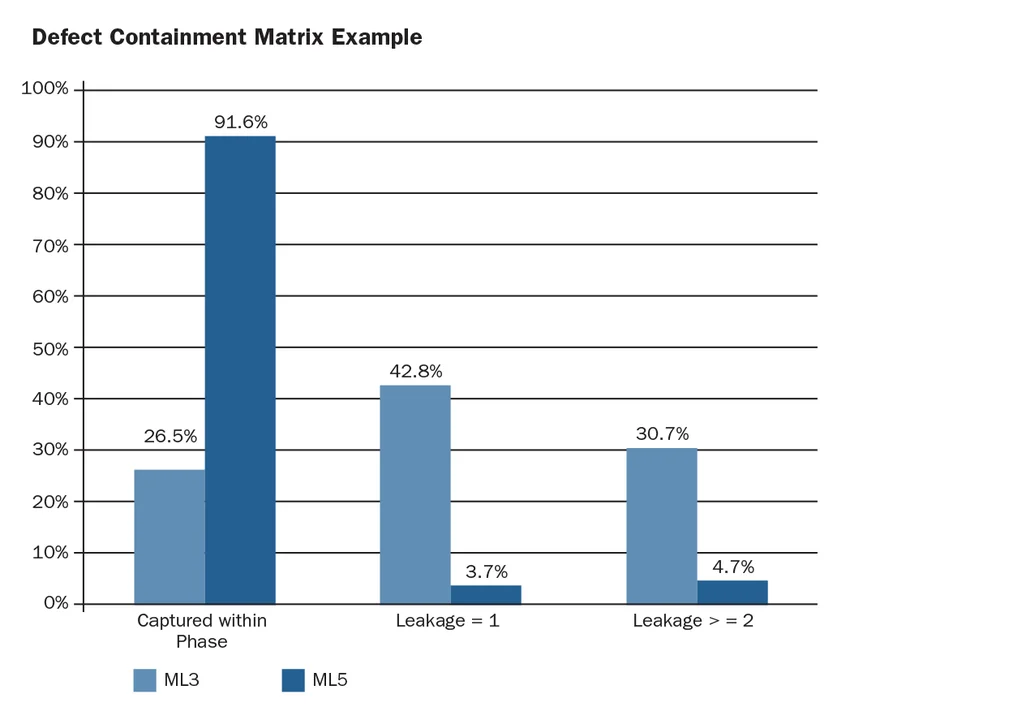
Source: ARDEC Weaponry Software Application Engineering Center (Picatinny Toolbox)
DCM was presented when The U.S. Army Weaponry Research Study, Advancement and Engineering Center (ARDEC) was at maturity level 3 in CMMI and starting its measurement of enhancement activities, among which was DCM. When it accomplished CMMI maturity level 5 a number of years later on, it determined the distinction and found the enhanced containment and decreased leak displayed in the chart above and laid out listed below:
- Flaws recorded within a stage increased by more than 3 times; flaw leak for one stage reduced by more than 11 times: and flaw leak for more than one stage reduced by more than 6 times.
- Less remodel happened late in the lifecycle when it is most costly to fix, leading to decreased expense and schedule threats.
- Peer examines ended up being more efficient in assaulting systemic problems. Peer evaluation roi ~ 5.5.
Effective Agile Updates
At Redstone Toolbox in Huntsville, AL the Software Application Engineering Directorate (SED) started a significant restructuring of the launcher abilities for the Accuracy Fires Rocket and Rocket System (PFRMS) For many years of ability enhancement on the launcher, the variety of computer system setup products (CSCIs) had actually grown to 36, as it was regularly simpler to concentrate on a brand-new section than to restructure. The software application size reached about 1.2 MSLOC. The Huntsville group handled a re-architecting of the system to remove redundant aspects into 6 CSCI’s, and a decrease to about 450 KLOC, about one-third its previous size. The restructure considerably reduced upkeep checks– a considerable worth provided to the warfighter in the field. While subjects like software application dependability are perfectly covered in other blog sites, it is very important to keep in mind that the code clean-up decreases the possibility of software application shortages in the field.
The group dealing with the restructure was likewise leading the shift into nimble advancement, producing brand-new metrics that much better explain developmental development when utilizing nimble approaches. The economical success accomplished utilizing nimble approaches at SED has actually led the Army program workplace to appoint more software application sustainment efforts for the launcher to SED.
Architecture Analysis and Style Language (AADL)
A variety of years earlier, the SEI teamed with SED in an effort to enhance software-reliant systems through virtual system combination with the Architecture Analysis and Style Language ( AADL), which is the market basic modeling language that was standardized by SAE International. As gone over thoroughly in a series of SEI post, AADL offers notations for catching tradition software application and system architectures and after that assessing the results of modification through predictive, quantitative analysis. Analysis domains of issue is crucial to software-reliant systems and consists of elements (such as hardware usage, system timing, latency results, scheduling, fault proliferation, fault tolerance, security, and security) that can just be comprehended from an architectural point of view.
With the SED at Redstone Toolbox, we once again see a sustainment-focused company associated with turning leading-edge research study into useful services for issues dealt with when updating and progressing tradition weapons systems. By using AADL to design alternative architectures and user interface alternatives for brand-new avionics in airplane like the Apache AH-46E pointed out above, SED can check out and confirm more secure and more effective upgrades to the weapon systems’ abilities with the prime professional. SED can then assess the result of modifications proposed by the prime professional for the program workplace. This evaluation might lead to an enhanced method as alternatives are examined or lead to the early discovery of system problems. SED and the SEI are likewise associated with innovative system advancement experiments for brand-new airplane systems as an outcome of this field research study with existing systems.
For instance, failure modes and results analysis are far simpler when an innovative style language like AADL offers exposure into the manner ins which mistakes can propagate throughout the system of systems that makes up a modern-day airplane. Likewise, SED can improve the security of the weapon system by utilizing AADL tools to examine security vulnerabilities and prevent them in the prepared upgrade. An earlier post explains how to design system habits with AADL Another post goes over using the language to record security and dependability elements To learn more about other applications of AADL, please visit our blog site landing page and click the AADL classification
Agile Systems Engineering
Another task at SED shows the worth of efficient combination of enhanced approaches for both software and hardware. The directorate had actually established knowledge in software application style that caused its classification as the center to establish and keep the game-based training of young soldiers– now called the “ America’s Army” item suite
The directorate found out of a requirement to establish a various software and hardware system– a simulator to train releasing soldiers on effective operations for each team station in a my own resistant ambush safeguarded (MRAP) automobile to consist of egress training after a rollover. These cars had actually supplied essential enhancement in the security of the soldiers inside it compared to earlier cars. Nevertheless, their style likewise increased the possibility of a rollover, so egress training– to enable escape from a reversed automobile– was required.
I utilized the term “nimble systems engineering” to indicate the ingenious method required to produce an option to this training obstacle. The SED task paired its video game abilities with some hardware partners who became part of the SED group. Within 18 months, it established a model of the system within the time typically invested attempting to get the requirements composed. All the model advancement was finished with regular user participation, so the essential concepts of nimble advancement were being utilized. Furthermore, the mix of software and hardware advancement indicated that systems engineering dexterity was being strongly shown.
Conclusions and Looking Ahead
For more than 200 years, sustainment efforts throughout our military systems indicated restoring them to an appropriate state for reuse. As the abilities have actually ended up being progressively software-reliant, nevertheless, the sustainment section of the system lifecycle has actually altered considerably. The companies dedicated to updating our military abilities have actually shown their knowledge and their capability to innovate with methods and tools newly out of the research study domain. Future blog sites will take a look at other examples from comparable SEI research study efforts.
Extra Resources
To check out the SEI technical report, Sustaining Software Application Intensive Systems, please check out https://resources.sei.cmu.edu/library/asset-view.cfm?assetID=7865