Cybersecurity costs business billions of dollars a year, with that expense anticipated to be in trillions by 2025, according to some cybersecurity research study companies Think about the Marriott hotels’ leakage of 500 million client records for which Marriott took a $126 million charge; and Equifax, an American credit reporting firm, invested 1.4 billion dollars on clean-up expenses related to the 2017 information breach of 150 million individual credit rating.
The typical expense of an information breach in 2020 is $3.92 million. Beyond financial ramifications, a big security event has the prospective to annihilate a business’s brand name and even be a career-ending occasion for the magnates.
The previous couple of years have actually taught us that every layer of the stack– from hardware all the method to JavaScript in a web internet browser– can have security vulnerabilities. In the meantime, security has actually progressed to be a cumulative obligation of everybody structure and running IT systems, consisting of designers, as business IT leaders acknowledge that security should be incorporated and constant in today’s cloud natural environments.
In “ Protecting Cloud Applications on Kubernetes,” we comprehend that computer system security is a huge field with several innovations that need to be discovered separately, then integrated properly in an application. Application designers and designers usually find out security innovations on the task when they initially experience them while under pressure to provide item functions and bug repairs. Checking out article, cutting and pasting setup settings, and browsing stackoverflow.com for assistance while under pressure to provide leaves designers seeming like they do not comprehend security however likewise do not have the time and resources to effectively discover it.
Understanding application security
Application security remains in the middle of its own improvement. It’s not just acknowledged as an essential discipline, it’s likewise entered into the everyday work of numerous groups, consisting of app designers. The increased concentrate on security by senior magnate impacts application designers in numerous methods:
- Utilize all item security functions: CISOs anticipate designers to utilize every security function readily available in items to protect an application. Do you understand how to set up and utilize the security functions in the application server, database, things shop, message broker, API entrance, service mesh, cloud services, configuring language and advancement structures being utilized on a task you are dealing with? It is no longer adequate to understand how to utilize an item, you need to understand how to utilize it safely.
- Follow business security requirements: CISOs anticipate applications to pass rigorous business security evaluations and audits. As a designer you need to have the ability to discuss to assessors and auditors how your application fulfills business security requirements. This indicates you require to be able to speak the security language utilized by info security experts so you can prevent expensive removal work to repair security concerns late in the advancement cycle.
- Style and carry out protected applications: CISOs anticipate designers and designers to create and carry out protected applications. This indicates that you need to recognize with lots of security procedures and innovations needed to create and carry out protected applications.
- Enable DevSecOps Change: CISOs are investing greatly in breaking down the silos in between the advancement, operations, and security groups. This indicates that as a designer you require to end up being acquainted with brand-new tools, procedures, and practices utilized to carry out DevSecOps.
The diagram listed below offers a map of the broad locations of application security.
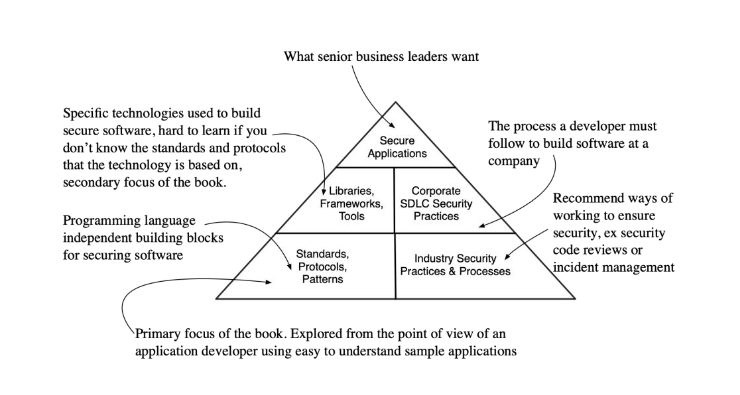
The top of the diagram above represents the objectives of senior magnate to develop protected applications that can withstand attacks. The greater layers of the diagram depend upon the layers listed below them. To protect an application you require to utilize security libraries, for instance a Java web application may utilize Spring Security to license user gain access to. Security libraries are insufficient to offer security, however. You need to create, code and keep the application in a safe method by following the business security practices for application advancement, for instance carrying out a security code evaluation, or setting code analyzers that identify typical security coding errors. As a designer you invest your time in the middle layer of the pyramid above.
Security libraries and structures carry out market basic procedures and patterns in a particular shows language.
The source of designer problems utilizing security libraires is absence of understanding about the underlying requirements, procedures and patterns the libraries carry out. If you comprehend the hidden security requirements, procedures, and finest practices you will discover security libraries and structures a lot easier to utilize and find out.
The initial step in the knowing journey is to develop a big-picture psychological design of application security usage cases and the readily available techniques for fixing them. We begin the finding out journey by evaluating 2 typical security issues:
- Protecting interaction channel
- Protecting application dependences
Analyzing how to protect interaction channels and application dependences allows us to understand kinds of abilities an application designer requires to learn about security and draw up a reliable technique for finding out security abilities.
Evaluate a typical set of security issues experienced when developing monolithic and microservice based applications so that you can have a big-picture understanding of the security innovations and requirements that every designer must recognize with in order to develop protected cloud native applications.
Protecting interaction channels
It is appealing to presume that there is no requirement to secure interactions in between the application backend and its database due to the fact that the traffic is on a “relied on” internal network.
It is a finest practice to run under the zero-trust networking design where you presume that the network is constantly untrusted. Deal with the internal information center network with the exact same level of suspicion that you deal with the web. As an application designer it is necessary that you demand Transportation Layer Security (TLS) all over for any application network interactions. Getting comfy with the TLS procedure is a vital security ability for designers. Mastering TLS allows you to:
- Compose protected applications that satisfy business security requirements.
- Rapidly set up TLS in your code without investing hours browsing blog sites and stackoverflow.com for setup guidelines.
- Debug connection concerns brought on by TLS setup settings quickly.
There is a twisted web of algorithms based upon deep lovely mathematics at the heart of TLS. You do not require to comprehend how these algorithms work or the mathematics behind them, however you need to comprehend what they do and how to configure them properly in your applications.
Protecting application dependences
Applications are constructed on top of numerous open-source libraries and exclusive software application elements. For instance, sometimes of composing I am dealing with a Spring Boot application that depends upon 106 open-source third-party libraries. I have actually seen some business applications with 250+ library dependences. Recycling software application elements throughout applications is a big time and expense saver, nevertheless it likewise presents the possibility for devastating security failures.
Supply chain security is a market large issue because every software application manufacturer depends upon external code providers who in turn depend upon other providers, and so on. Brand-new security tools and procedures need to be constructed then embraced extensively to protect the software application supply chain.
Constant automated reliance vulnerability detection
You can quickly identify susceptible dependences utilizing an automated vulnerability scanner. The vulnerability scanner develops a list of all the dependences an application utilizes by evaluating the application’s code, develop scripts and created artifacts. The scanner compares the application’s reliance variations versus a database of recognized vulnerabilities. If a match is discovered the scanner informs the advancement group.
Computer system security is an enormous subject with several subfields and expertises. It can take a life time to master computer system security. As a designer you need to concentrate on the subset of computer system security that is most pertinent to your requirements for composing protected applications.
Summary
- Never ever rely on the network: Deal with internal “protected” networks with the exact same level of trust as the web. Protect all application interaction channels utilizing TLS procedure.
- TLS is a crucial fundamental innovation that every designer must understand actually well.
- Software application supply chain attacks are increasing due to the fact that they are exceptionally reliable. Utilize a reliance vulnerability scanner in all your applications, quickly repair concerns flagged by the vulnerability scanners. Stay up to date with advances in software application supply chain security tools and procedures and promote their usage with your company.
- The objective of DevSecOps is to lower the time, effort, and expense of taking a company concept from idea to production while using the very best practices of security, operations and advancement.
- Security is the cumulative obligation of everybody operating in IT consisting of designers. Improving your security abilities makes you better to your company and allows you to solve security concerns rapidly.
( Excerpt from the pre-publication book “ Protecting Cloud Applications on Kubernetes” by Adib Saikali)
To read more about the transformative nature of cloud native applications and open source software application, join us at KubeCon + CloudNativeCon Europe 2023, hosted by the Cloud Native Computing Structure, which occurs from April 18-21.